Some techniques are more effective than others, and some are safer than others. Thoroughly examine these methods and try to view private Facebook profiles and extract data from them.
Technique #1: Hack Someone’s Facebook Messages Without Knowing Their Password
mSpy is an easy way to hack a Facebook account from your mobile device. It’s quick, easy, and very convenient.What makes this particular app great is the fact that it’s not actual hacking. That means that, by tracking someone’s cell phone, you won’t be breaking any laws, and can easily log into someone’s Facebook Messenger without them getting a notification. Plus, it also you to hack your target’s Snapchat and other social media accounts.
It is an entirely legitimate app that enables you to gain access to the following features:
- Accessing all sent, received, and deleted Facebook messages
- Facebook media files – images, videos, friend requests
- Tracking other Facebook Messenger activities
- Reading Instagram messages
- Call logs
- GPS location
- Sending fake text messages
- Deleting messages with flagged keywords
mSpy is suitable for both beginners, but also tech-savvy individuals.
Thanks to this spying app, you can control all Facebook and other social apps, account profile, and functions from a single control panel. Moreover, the installation is very straightforward.
All you need to do is → purchase a subscription plan → download the app → install it on the targeted device, and that’s it.
Bear in mind, though, that rooting might be required to gain access to target account functions (Android only).
How to Hack a Facebook Account on Mobile Phone Remotely
To hack someone’s account ID remotely, you need to know their iCloud credentials. If you don’t know their credentials, you’ll need to jailbreak their iOS. Moreover, this Facebook hack method doesn’t work on Android devices. Here is how to hack Facebook account on mobile phones:You’ll need an active mSpy subscription to get started. As such, this will involve creating a free mSpy account then picking a subscription of your choice.
To kick things off, here’s what you’ll do:
Step 1: Navigate to mSpy’s website and click on the green “Try Now” button on the top navigation bar.
Step 2: Enter your email and complete the wizard by picking a subscription plan of choice.
Step 3: Get the login credentials from your email and use them to login to mSpy’s control panel.
Step 4: On the dashboard, select Android as the target device and fill in the kid’s name, age, and device model.
Step 5: On the target device, open the Play Store app and then navigate to Play Protect > Settings (Cogwheel Icon).
Step 6: Turn off both options under Play Protect Settings i.e. Scan apps with Play Protect – Disabled, Improve harmful app detection – Disabled.
Part 2 – mSpy Installation and Download
Still on mSpy’s setup wizard, you’ll now get the download link to use. Note that you’ll need to download the app on the target phone.This is how to carry on with the process:
Step 1: Open a browser of your choice and key in the download link on the address bar and hit enter.
Step 2: Complete the verification captcha to download mSpy’s APK file.
Step 3: Once the download is complete, tap on the APK file and enable “Install from unknown sources” if prompted.
Step 4: Tap on the “Install” button to begin the installation process.
Step 5: Click on “Don’t remind me again” in case a virus notification popup appears on the screen and hit “Ignore”.
Step 6: Tap on “Open” so that you can begin mSpy setup wizard.
Requirements:
- Physical access to the Android device
- Active mSpy subscription
- Active internet connection
Technique #2: Reset the Password
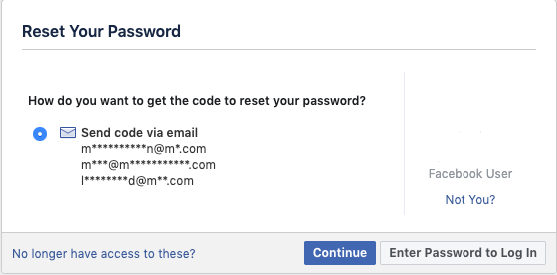
While most people might have a password protecting their socials at all times, they hardly ever do this for their email address accounts. This is the ultimate rookie mistake that, lucky for you, is the jackpot of account hacking gold.If you have physical access to your target phone and know the email address associated with their Facebook account, simply:Go to Facebook and click on “Find your account.”
Confirm the email address where it is going to be sent the code.
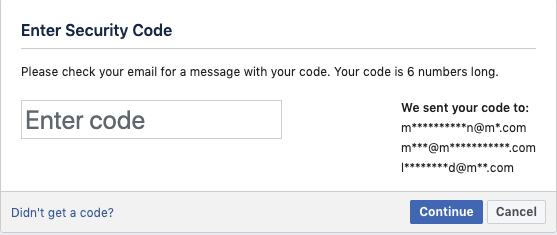
Once the password reset link is sent to their email address, enter the security code.
Ensure you delete the email with the reset link to cover your tracks.
Choose the new password.
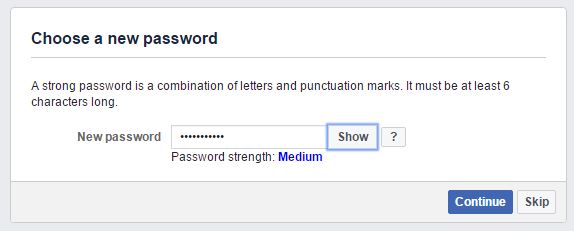
Choose the new password.
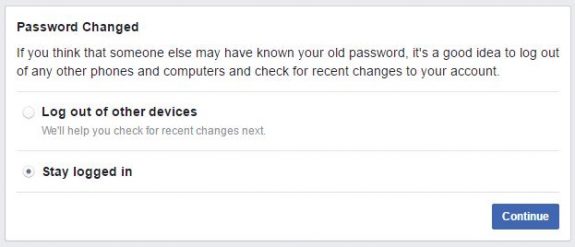
Choose to “stay logged in.”
If the target person has two-step verification enabled, you’ll find online programs that allow you to divert the One-Time Passcode (OTP) from the target account phone number to yours. However, you’ll need to answer a few security questions.
It refers to the use of various psychological methods to manipulate people into divulging sensitive information. According to a recent survey by Avast, a whopping 83% of people use weak passwords.
These are some of the most common weak password combinations:Name + date of birth
Moreover, if you don’t manage to guess it, then you might have to reset it by entering an answer to a pre-set security question. The most common security questions include:
If the target person has two-step verification enabled, you’ll find online programs that allow you to divert the One-Time Passcode (OTP) from the target account phone number to yours. However, you’ll need to answer a few security questions.
Technique #3: Guess the Password
If you want to learn how to hack someone’s Facebook ID, try guessing their password.It refers to the use of various psychological methods to manipulate people into divulging sensitive information. According to a recent survey by Avast, a whopping 83% of people use weak passwords.
These are some of the most common weak password combinations:Name + date of birth
- Name + year of birth
- 123456789
- 987654321
- Their kids’ names
- Their significant others’ names
- Anniversary dates
- Pet names
- Other meaningful information/cell phone number/numbers/dates/names
Moreover, if you don’t manage to guess it, then you might have to reset it by entering an answer to a pre-set security question. The most common security questions include:
- Favorite teacher
- First pet’s name
- Place of birth
- Anniversary date
- Mother’s maiden name
Technique #4: Man-in-the-Middle Attack
Ever wondered why it’s not safe to use public Wi-Fi to access your social media accounts or any other site that requires you to enter your personal information? Well, it’s because there could be a “man in the middle”…Man-in-the-middle (MITM) attack is among the most effective methods of hacking someone. However, bear in mind that this technique is illegal, and if not done securely, you might face charges.
The technique exploits the Wi-Fi network’s security limitations to access users’ passwords.
You can read the full guide here, but we’ve summed up the surprisingly simple process:
Requirements:
- Kali Linux operating system
- Good command of network interface
- Good knowledge of executing command lines
- Find out the name of the network interface.
- Obtain the IP addresses of the Wi-Fi router you’ll infiltrate.
- Target device IP
How to do it:
- Obtain the network interface name by running the ipconfig command on a terminal.
- Copy the name of the desired interface and save it.
- Obtain the router’s IP address by executing the IP route show command on a terminal.
- Obtain the victim’s IP address by using a Network Monitoring Software Tool.
- Enable IPv4 packet forwarding in Linux by executing the following command in a new terminal: sysctl -w net.ipv4.ip_forward=1
- Intercept packets from the victim by using arpspoof. This is the overall structure of the command: arpspoof -i [Network Interface Name] -t [Victim IP] [Router IP]. Example: arpspoof -i wlan0 -t 192.000.000.52 192.000.000.1
- Let the command run – don’t stop it.
- Intercept packets from the router by using arpspoof spoofing program code. Execute the following command: arpspoof -i [Network Interface Name] -t [Router IP] [Victim IP].
- Let the command run – don’t stop it.
- Sniff images from victim navigation by using Driftnet. Driftnet is a program that is used to listen to network traffic and take images from TCP streams. This is the structure of the driftnet command: driftnet -i [Network Interface Name].
- Sniff URL information from victim navigation by using urlsnarf. This command enables you to sniff all HTTP requests following a Common Log format. Execute the following command: urlsnarf -i [Network interface name].
- Once done, disable packet forwarding by executing the following command: sysctl -w net.ipv4.ip_forward=0.
You’ll now be able to access the individual’s Facebook messages and read their conversations.
Technique #5: Phishing
Phishing is a technique that is commonly used by beginner-level hackers to obtain credentials and other sensitive information from victims. The whole method is based on the fact that the attacker creates a fake website that resembles the original one (e.g., Facebook), and convinces the victim to enter their Facebook login information on the fake website login page.Requirements:
- Internet connection
- A fake phishing page – website
- Decent design and persuasion skills
Instructions:
- Go to Facebook.com and ensure that you’re logged out of your account.
- Open the View Page Source tab by pressing Ctrl + U.
- Once you see the source code, select it, copy it, and paste it in a notepad. You can perform this by pressing Ctrl + F.
- Once the code has been copied onto a notepad, you have to type the word action into the notepad as well. This will allow you to locate the action attribute of the login form in the source code.
- Then, replace the action attribute with process.php
- Perform a search once again, to ensure that your text is similar to this: action=’’https://www.facebook.com/login.php?login_attempt=1&lwv=111.’’
- Then, use the Inspect Element option by pressing Ctrl + Shift + I.
- Delete all text that is highlighted in green color and replace it with post.php. It should look like =post.php.
- The next step is to ensure that you save all the information above on your hard drive. Save it as index.htm.
- Next, you need to create a.php file. Open a new notepad page, copy the code, and save it as post.php.
- Find a free website hosting service, sign up, and log into your newly created account.
- Open the control panel, locate the file manager feature and move to public_html.
- Delete the default .php file and upload the previously created index.htm and post.php by pressing the upload button. Upload the files one at a time.
- Next, open the index.htm file, and you’ll see an identical replica of the original Facebook page.
- The last step is to copy the URL of your new page, send it to the victim, and convince them to use that link to log in. When they do, you will receive their Facebook login credentials, and they will be redirected to the actual Facebook login details page. That’s it – now you can read their Facebook messages.
Once the victim realizes that the password has been reset, they will create a new password, and you will be logged out. Also, if the victim enabled two-factor authentication, it would be harder to implement the attack.
Technique #6: Use a Keylogger
A keylogger is a great tool that enables you to receive all keystrokes that have been made on the victim’s computer.This method requires physical access, though.
You need to install the keylogger on the victim’s target device to be able to see what they’re typing. The installation process is rather easy: You need to → purchase a subscription plan → install the software → and that’s pretty much it.
Once done, you will be able to see everything that the victim is typing, including their Facebook email address and password.
Technique #7: Exploit the SS7 Vulnerability
This is an advanced method that is not suitable for all devices.The SS7 Vulnerability enables hackers and intelligence agencies to monitor unknowing users with ease without special surveillance software.
SS7, or Signalling System Number 7, is a signaling protocol that is used by over 800 different service providers across the globe.
The issue with SS7 is that it trusts all text messages, regardless of their content or origin. That means that the devices could be easily fooled into providing sensitive information.
Requirements:
- The target’s mobile phone number
- Linux OS
- SS7 SDK
Instructions:
- Register the victim’s mobile phone number on a fake MSC node.
- The real HLR will set a new location for the account owner’s cell phone number.
- Open the Forgot Your Password option on Facebook.
- Enter the user’s cell phone number.
- The original MSC will transform the SMS into SMS-C.
- The real SMS-C will contact HLR and ask for the victim’s location.
- The real HLR will reply by providing an MSC address, which is fake.
- The two-factor authentication recovery code will be intercepted and diverted to your device.
- Then, you can reset the password and gain access to the victim’s FB account.
Technique #8: Use Online Hacking Tools
There are specific online tools that claim that they can hack any Facebook account for free in a matter of seconds.Supposedly, all you need to do is to enter a unique Facebook user ID, and you’ll receive a password.
Beware of these websites, as they’re usually fake. Not a single professional hacker would ever advertise their services for free in the public internet domain. The goal of these websites is to either plant malware on your device or to steal your data.
Moreover, there isn’t such a thing as a quick fix for stealing someone’s Facebook password.
If that were the case, everyone’s user accounts would be hacked continuously. There have been numerous instances where people were attacked by ransomware through these websites and had to pay large sums of money to retrieve access to their devices.
So, our advice is to stay as far away from these free hacking websites as possible.
Technique #9: Code Your Way
Now, bear in mind that this method is a bit more advanced and it will take time and patience to execute. Moreover, we strongly advise you against trying it because it might result in legal consequences. Check your local laws and regulations first.Below, you will find a quick rundown of how this process looks like, but if you’d like to see a full instructional manual, you can check out this Codescracker article.
The programming languages you will need:
- HTML
- CSS
- JavaScript
- PHP and MySQLi
Step 1: Make a copy of the original Facebook accounts page.
Follow the tips below:
- Check the target’s preferences
- Create a message that’s related to their preferences or hobbies
- Copy the login code from Codescracker’s website.
- Install the XAMPP software
- Save the code and put an image that corresponds to your message
- Open XAMPP, start Apache and SQL module and put the redirection code on the top of the page.
Step 2: Write a script to store their Facebook credentials:
- Copy the code from Codescracker’s website.
- Place it in the same directory as the file above.
- Name it login.php
Step 3: Redirect your target to the real Facebook page so you don’t raise any suspicions:Copy this redirect code and implement it.
Step 4: Create a database to store said ID credentials and passwords:
- Use XAMPP and SQL to execute this task.
- Fill in the columns.
- Save everything.
Step 5: Send the link to your target.
Step 6: Extract the data from your database.
Technique #10: Social Engineering
Social engineering is a technique that is based on convincing the account owner that you’re a legitimate person or an organization.The whole goal is to persuade them to provide you with a password, usually by clicking a link. A phishing attack and social engineering are somewhat similar; the only difference being the social aspect.
In phishing, you don’t have to do a lot of convincing. All you need is to create fake login pages and prompt the victim to enter their credentials there.
However, social engineering requires a bit more effort. You need to seem very trustworthy. There is a wide variety of ways to perform this type of hack to obtain one’s Facebook password.
Here is a more generalized step-by-step hacking guide that can be adjusted as you see fit:
- Think of a legitimate organization that you’d like to impersonate – in this case, Facebook.
- Create a fake website with a similar domain name. For example, faceboook.com, facebooknetwork.com, or something else that is as similar to the original as possible.
- Create an email address using the website domain.
- Find a legitimate person who works at Facebook through LinkedIn and use their name when creating the email address. The website must look legit, and your email account has to have a signature and a Facebook logo.
- Find the victim’s email address and write an email that is titled something along the lines of “Your Facebook account has been hacked,” or “Your Facebook account needs URGENT assistance.” The whole goal is to make the email seem urgent, to entice the victim into clicking the link to your website.
- Tell them that they need to log into their account through your link for further assistance.
- Once they do, you will receive their email address and password.
Bear in mind that sometimes, these types of emails end up in the Spam folder, , so this method might not always work
Technique #11: Use Target ID
The last method we will discuss is quite simple yet effective. However, it won’t work for users that are based in Canada and the US. Here’s how to do it:- Open the victim’s Facebook profile.
- Locate the Poke menu, right-click it, and choose the Copy Link option. The link should resemble this one: http://www.facebook.com/profile.php?id=VICTIM’S ID.
- Open your address bar and type in the following code: javascript: Chat.openTab (VICTIM’S ID). The Victim’s ID should be the one you extracted from their Facebook profile link.
- Then, press Enter. You will see the victim’s activity history, including Facebook text messages.
How to Get Someone’s Facebook Password Without Changing It?
If you want to get someone’s Facebook password without changing it, you can choose from two options of going about it. The first is to use a keylogger to track the user’s keystrokes on the target device. This way, whenever the user enters their Facebook password, the keylogger will automatically record the keystrokes, thus giving you access to the password without changing it.One such keylogger is mSpy, which has been discussed above. While mSpy worked as an effective parental control tool and best hidden spy app, it also doubles up as a keylogger that you can use to find someone’s Facebook password.
The other method to get someone’s Facebook password is more technical and works well if you’ve got the appetite and the know-how to do it. It requires a computer or laptop and an active internet connection. Here’s how it works:
- Visit the Facebook website through the web browser.
- Log into your account to get access to the search box and type in the name of the person whose account password you want.
- The next step is to copy the target’s username from their Facebook URL in the URL bar. For example, if the URL reads facebook.com/abcde, you need to copy ‘abcde.’
- You can then use a tool like Ninja Facebook ID Lookup to get a hold of their email address registered with their Facebook account. However, the only drawback about this is that you’ll only be able to access this information if the target’s profile is public.
- Once you get the email address, go back to Facebook and enter it into the email section and then right click > Inspect Element.
- You will see a line that reads < input type=”password”
- Change the type from “password” to “text,” and you will have access to the user’s Facebook password without changing it.
How to Find Out Someone’s Facebook Password?
The best way to get someone’s password is to use mSpy’s keylogging feature. Just install mSpy on the target phone and let it do its magic. The keylogger feature records all keystrokes the phone user makes, meaning that you can easily get their Facebook password and email. Plus, you can also read Facebook messages and check likes.Conclusion
So, there are several methods of tracking Facebook user accounts, and using Facebook tracking apps for hacking someone’s Facebook is the best of them. What’s great about these apps is that you can use them for other activities like tracking someone’s SMS without their mobile device – read more in this blog post.If you have any questions, please leave them in the comments. or chat with our team of expert via our whatsapp number or livechat when registered as our member.





Post a Comment